Web services attacks are a type of cyber-attack that target web-based applications and services. These attacks are designed to exploit vulnerabilities in web services, which can lead to data theft, system downtime, and other security breaches. In this blog, we will be discussing more about the “SOAP” web service and “RESTful” web service. The following is a list of groups that are currently active:
Table of Contents
ToggleWhat Do you Mean by Web-Services?
Web Services allow applications to communicate with each other independent of platform or language. In the current day, many applications and web pages depend upon web services to seamlessly exchange information with one another. Web services provide a way to transfer dissimilar data over the network helping organizations/individuals reuse functionality across services. There is a dynamic relationship between the user and the web service, as many scenarios are user input controlled.
Web services protocols include Simple Object Access Protocol (SOAP), XML-RPC, and JSON-RPC for message communication; Web Service Description Language (WSDL) and Universal Directory and Discovery Integration
(UDDI) for web service description and discovery. Frameworks used for creating/developing web services mainly include Apache Axis, .NET and Zend.
There are two types of web services.
- SOAP Web-Services
- RESTful Web-Services
SOAP Web Services:
It is an XML-based protocol having the main benefit of implementing the SOAP Web Service as its security. The abbreviation of SOAP is the Simple Object Access Protocol. SOAP offers a wrapper for sending web service-based messages over the Internet with the help of HTTP protocol. All its messages are usually in XML format. The SOAP message consists of the following:
- SOAP document has a root element termed as the <Envelope> element. This element is the initial element used in an XML document.
- Then next to the “envelope,” which is categorized into two parts. The former is the ‘header,’ and the latter is the ‘body.’ The ‘header’ includes the routing-data that is essentially the information telling the XML document to whom or for which the client needs to be sent.
- The ‘body’ contains request and response information in the XML format. It defines the actual content of the message to be sent between the client and the webserver.
- The SOAP Fault element is an optional element used to display an error message encountered during the transmission of a SOAP message. It holds the status of SOAP messages and errors.

Fig: SOAP Structure
Common Vulnerabilities in SOAP are: –
- X-PATH Injection
- SOAP Injections (SQL, XML, XAML, Command Injection)
- Denial Of Services (DOS)
- Cross-site Scripting
- Sensitive Data Exposure
- SOAP Action Spoofing
- SAML Vulnerabilities
- Replay Attacks
How to Test SOAP Web-Service?
There are few test cases that can be used while testing SOAP Web-Service.
Generic Injections: Injections like SQL injection, XML injection, and X-PATH injection can lead to access to the database. As you can see in the below image, an application makes an API call to fetch the passphrase of a user.
- It makes a “GET” request to the server and includes a username in its request.
- URL. This behavior can be exploited by executing an SQL Injection attack.

Fig: Vulnerable API Endpoint
- Injecting a single quote (‘) after the username to generate an error. From the below image it is confirmed that a SQL injection might be possible here.

Fig: Executing SQL Injection Attack
- Try to trigger responses using Boolean equation. “’ or 1=1”. Below shows a valid response for a true value of the Boolean equation.
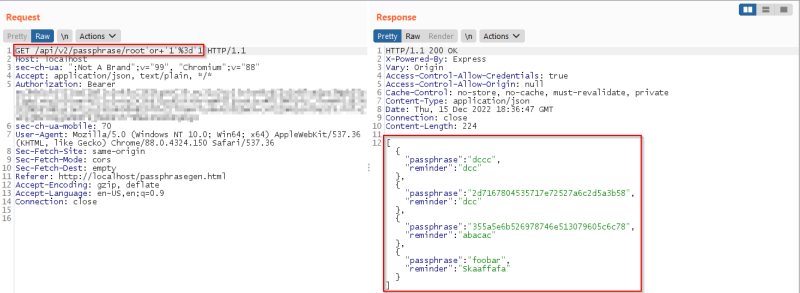
Fig: Boolean Based SQL Injection Attack
- Broken Access Controls: Access control vulnerabilities that can grant access to the resources beyond the attacker’s privileges.
- DOS Attacks: Denial of Services attack that can lead to stopping the services.
- Excessive Data exposure in response: Sensitive data leaked in the response can be used by an attacker to gain access to highly privileged user roles. The below image is from a vulnerable DVWS application that shows an API endpoint discloses sensitive information including “admin” user.

Fig: Excessive Data Exposure
- Invalid Types: As the name suggests, the invalid types are used to check and exploit all invalid input data used in a web service.
- Boundary Scan: The Boundary-scan security test is used to check the poor handling of the web service values outside of the range definition.
- Malformed XML: Malformed XML security scans are used to check and exploit poor handling of the invalid XML that can be rendered either on a web server or in a web service.
- Malicious Attachment: Malicious security attachments are used to scan all bad handling of the attached files.
- Custom Scripts: Custom scripts are a type of security scan that allows us to use scripts to create custom parameters that cover up values.
- XML Bomb: The term XML Bomb is a type of Security scan used to handle the malicious XML request that can corrupt the whole web service on the server or steal some sensitive information.
RESTful Web-Services
RESTful Web-Service: REST stands for Representational State Transfer. It is an architectural style that provides standards between computer systems on a web service. The purpose of developing a “RESTful web-service” is to make the web service more effective. RESTful web-service is stateless and simpler than SOAP web-service. It supports JSON as well as XML. It follows standard protocol such as HTTP, HTTPS and FTP.

Fig: RESTful Structure
There are some vulnerabilities which are common in SOAP and REST web services.
Common Vulnerabilities in RESTful Web-Service and SOAP Web-Services are: –
- Injections.
- XXE. (By manipulating the “Content-Type”)
- Cross-site Scripting.
- Cross-site Request Forgery.
- Broken Access Controls.
- Authentication Attack.
- Sensitive Data Exposure.
- Denial of Services (DOS).
- Mass Assignment.
- CORS.
Some vulnerabilities that differ in RESTful web-services are: –
How to Test RESTful Web-Services?
There are few test cases that can be used while testing RESTful web-services.
Some of the test cases are common in SOAP and RESTful web-services.
Common test cases are:
- Broken Access Controls.
- Tampering with HTTP Methods.
- Input Validation.
- Error Handling
- Sensitive Information in HTTP Request.
- CORS.
Some test cases are different because of using JSON for passing the data and use of JWT’s for Authorization. These test cases are: –
- Attacking JWT Tokens: JWT Tokens are the standardized format of sending cryptographically signed JSON data between systems. A JWT consists of 3 parts: a header, a payload, and a signature. Attacking a JWT involves modifying the tokens and sending them to the server in order to bypass the access controls. These JWT attacks involve exploiting weak signature verification, accepting tokens with no signature, brute-forcing the secret keys.
- Testing for JSON Injections: Since the sensitive information is transmitted in the JSON format, the RESTful web-services are prone to attacks such as JSON injections, JSON hijacking. JSON Injections occur when the data from an untrusted source is not sanitized by the server and written directly to a JSON stream. This is called Server-side JSON Injection, whereas when the data from an untrusted source is not sanitized and parsed directly using the JavaScript eval function. This is called Client-side JSON Injection.

Fig: JSON Injection Tampering price.

Fig: JSON Injection. Manipulated price.
- Mass Assignments: Mass Assignment is a vulnerability where an active record pattern is manipulated into modifying data items that should normally restrict user functions such as passwords, granted permissions, or admin access.
This vulnerability arises when objects at the back-end, e.g., database records, are created by using the object representation received with the client request including fields that are not supposed to be altered. Thus, an attacker can gain privileges on sensitive functionalities and potentially compromise the application’s confidentiality, integrity, and availability.
Conclusion
Here we conclude that the above-mentioned attacks are widely used while attacking web-services. Web services are more likely to be prone to such attacks because they expose the functionality of the website to the outside world so that other applications can use it.
Reference Links: –



